Why Skyflow?
Sensitive data is the lifeblood of every modern business. As companies collect more data, the risk of breaches grows, forcing them into a difficult tradeoff: protecting sensitive information or maintaining its usability.
One option is to apply the most advanced encryption techniques to secure the data, essentially “locking it up and throwing away the key.” While this ensures the data is safe, it becomes unusable.
Neither extreme offers a complete solution. Striking a balance between security and usability is critical for safeguarding both business operations and customer trust. But how can companies achieve this balance while addressing a range of complex challenges, including
- Protecting Personally Identifiable Information (PII): Protect PII and manage the flow of data across the tech stack
- Protecting Payment Card Information (PCI): Protect PCI for compliance while having more control
- Managing Data Residency: Collect, manage, and use regulated data while complying with global data residency laws
- Powering analytics: Analyze PII for marketing, customer service, and more—without risking data privacy
- Managing Gen AI Data Privacy: Keep sensitive data out of Gen AI models, applications, and agents
Do you handle the complexity of integrating many-point solutions to discuss each need individually, or is there a tool that can effectively tackle them all at once? How can developers manage these problems? That’s where Skyflow and data privacy vaults come in.
But what exactly is a data privacy vault?
Tech giants like Apple, Google, and Netflix developed the Data Privacy Vault architecture to address the challenges of securing sensitive information while ensuring compliance with fast-evolving data protection regulations. The IEEE has since recognized it as the recommended approach for securing sensitive data.
- Isolate: Vaults are segregated from your other infrastructure and services and are only available through privileged access.
- Protect: Vaults employ encryption, tokenization, masking, and other privacy-preserving technologies to secure sensitive data.
- Govern: Vaults have built-in data governance tools to enforce granular access control policies.
- Use: Vaults offer features that allow data to be used securely by people or integrated into workflows, such as privacy-preserving analytics, Gen AI applications, agents, and first- or third-party integrations.
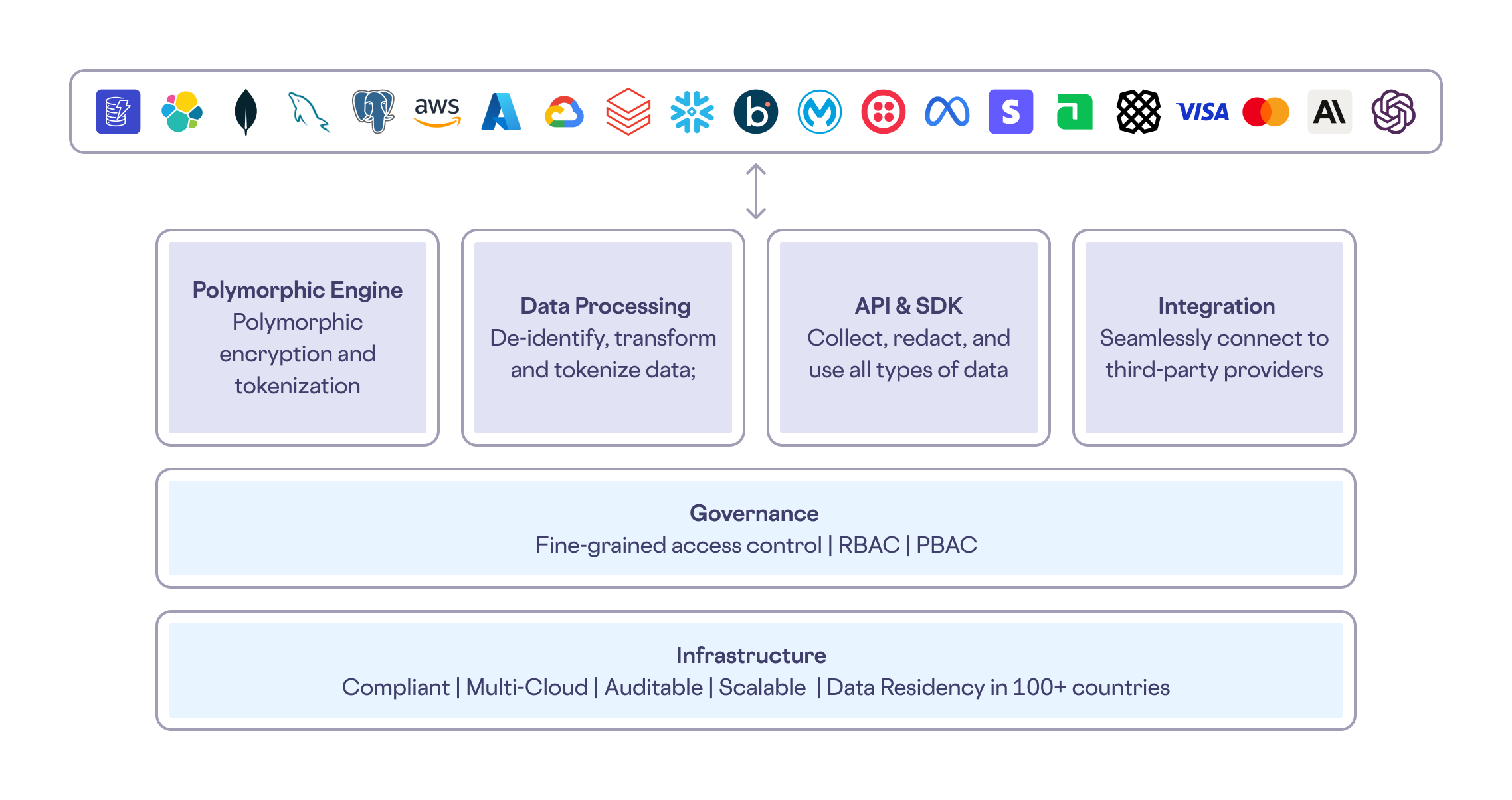
The Skyflow Data Privacy Vault
Skyflow empowers developers at companies of all sizes with a state-of-the-art Data Privacy Vault without a hefty investment of time and resources like what Shopify built internally.
The Vault includes:
- Infrastructure:
- Scalable infrastructure satisfying data residency regulations across 100+ countries.
- Compliant with multiple frameworks (SOC 2, PCI DSS, HIPAA, and more).
- Deployment isolated in a Virtual Private Cloud (VPC), available in different models: multi-tenant, dedicated VPC, or your cloud.
- Governance
- Policy-Based Access Control (PBAC) model for sensitive data usage and de-identification, deployed in companies ranging from high-growth startups to Fortune 500 companies.
- Context aware authorization to enforce granular row level security.
- Polymorphic Engine:
- Transformation and usage of both unstructured and structured data secured via patented polymorphic encryption techniques and tokenization.
- Full or partial masking of data based on the usage
- Solving for common use cases like Personally Identifiable Information (PII), Payment Card Industry (PCI), Protected Health Information (PHI), and any other types of sensitive data.
- Data Processing:
- Import, tokenize, and detokenize large volumes of data from varied sources using Pipelines while programmatically de-identifying sensitive data using the Detect API.
- Ensure a seamless migration of existing tokens by inserting your tokens into a vault alongside your data.
- APIs and SDKs:
- Build secure integrations and UI to collect, redact and use sensitive data while continuing to be compliant and not compromising security or privacy of sensitive information
- Integrations:
- Safely interact with 40+ third-party systems like payment processors, data stores, LLMs, and more while building custom workflows tied with other internal services using Connections and Functions.
Governance
Skyflow Data Privacy Vault has a sophisticated Policy-Based Access Control (PBAC) governance engine built in, inheriting the best features of
- Role-Based Access Control (RBAC): Assign roles to users and machine identities across accounts, workspaces, and vaults through an interface and programmatically
- Attribute-Based Access Control (ABAC): Define context to enforce access even at the row-level
Skyflow’s policy-expression language defines policies that attach to roles, which you can then assign to users and machine identities (service accounts). Skyflow also offers context-aware authorization, allowing you to pass more context to each claim to enforce granular row-level security based on the data requester’s context.
Policies such as this one can then be attached to roles, which are assigned to both users and machine identities. This ensures governed access to the data from both people and downstream applications.
Visit Access Control to learn more.
Data processing
Skyflow vaults enable developers to leverage the value of sensitive data when working with third parties. Developers can work directly with sensitive data without bringing it into their infrastructure or services. Developers achieve this without having to provision or manage the compute infrastructure themselves.
Skyflow’s pipelines allow securely importing, tokenizing, and detokenizing large volumes of data from source systems like S3 buckets, FTPS servers, and SFTP servers. Pipelines can also de-identify sensitive data during migration. Pipelines can perform the below actions:
- Import: Upsert data and create Skyflow ID for each record
- Tokenize: Return a file that has sensitive data replaced by tokens
- Detokenize: Accept a source file containing tokens and replace with plain-text data
You can also configure Pipelines to insert your existing tokens into Skyflow for secure storage and usage. See Pipelines.
Data de-identification
To de-identify and remove secure data as you execute and run the preceding workflows, Skyflow offers a data detection and de-identification API. The Detect APIs perform sophisticated analysis across text, audio, and image data by leveraging advanced algorithms and ML techniques. This allows companies to securely use third parties without exposing any sensitive data. See Detect.
Integrations
Connections & Functions
To securely interact with third parties, Skyflow offers Connections. These proxy functions help you build your own connections to any first-party or third-party API to securely send and receive sensitive data. For instance, you want to send credit card data to your payments processor. With a connection, you can make a call to Stripe with tokenized credit card information. The connection routes the request through the vault, where the tokenized data is swapped for real values, and then sends it to Stripe.
Connections accept advanced authentication parameters and keys, offering support for mLTS and shared secrets, and support standards such as JSON Web Encryption (JWE) and JSON Web Signature (JWS) for encryption and digital signatures. See Connections.
In addition, Skyflow offers functions to add custom logic to the above workflows. You can develop custom code using Node.js to implement workflows that can be deployed and invoked through connections. Functions can be deployed for varied use cases like
- Transforming incoming data for usage by your backend systems or other services
- Generating reports for downstream services
- Send an identifier to a connection and upload a file protected in the vault to a document cloud service, like DocuSign
See Functions.
Technology Integrations
Skyflow integrates with 70+ third-party systems and is always adding more. Here are a few of the systems that Skyflow integrates:
- Data stores: Snowflake, Databricks, MongoDB
- Data processing pipelines: Mulesoft, Boomi
- Email and messaging: Sendgrid, Twillio
- CRMs: Salesforce, Hubspot
- Payment Service Providers (PSPs): Stripe, Adyen, Braintree, Cybersource, Checkout
- Money Movement: Dwolla, Moov, Nium
- Card Issuers: Marqeta, Visa, Mastercard, Apto
- Data providers: Plaid, Yodlee
See the Connections catalog for the full list.
Polymorphic engine
Skyflow transforms sensitive data, whether structured or unstructured, in the data privacy vault which has several privacy-preserving technologies built in. These technologies include, but are not limited to, polymorphic encryption, data de-identification, and tokenization.
- Polymorphic encryption: Data is encrypted using a variety of encryption schemes, which allows for users to perform certain operations on encrypted data, such as aggregation and comparison, without having to decrypt it.
- Data Masking: Upon retrieval, data can be dynamically de-identified depending on who is accessing the data. Skyflow offers powerful masking capabilities (for example, masking everything but the last 4 digits of a credit card) and can also redact sensitive data.
- Tokenization: Skyflow can generate tokens for sensitive data that can be safely stored on your infrastructure. Skyflow’s tokenization engine offers a variety of token types, including random tokens, format-preserving tokens, deterministic tokens, and more.
- De-identification : Detect sensitive data from within unstructured data and replace it with different types of tokens based on the usage of the data.
Skyflow’s polymorphic encryption, de-identification, and tokenization techniques scale to both structured and unstructured data through programmatic and manual techniques, such as file upload.
See Tokenization.
Infrastructure
Skyflow vaults are built on top of a highly scalable, enterprise-ready system. You can bring your customizable schema, and a robust key management option allows you to manage your encryption keys. The infrastructure that is the foundation for Skyflow vaults meets all of the following qualifications:
- Secure: The vault is isolated in a virtual private cloud (VPC) available in different deployment models from multi-tenant, dedicated VPC, to your cloud.
- Bring your own keys (BYOK): Support for bringing your own encryption keys and existing tokens.
- Highly available: It maintains high availability, so you don’t have to worry about infrastructure failures. Services are architected to transparently handle and recover from failures without service disruption or data loss with robust catastrophic disaster recovery.
- Compliant: It’s SOC2, HIPAA, and PCI compliant.
- Zero-trust: It continually verifies permissions and access.
- Global: It uses multi-zone and multi-region deployments help overcome network disruptions.
Skyflow offers unmatched flexibility in its deployment models, and deploys as
- Multi-tenant SaaS: The most popular option.
- Single-tenant SaaS: Used by mid-size and large enterprises with huge data volumes.
- Bring your own Cloud: For large enterprises with regulatory needs.
Vertical solutions for FinTech
Skyflow Data Privacy Vault offer purpose-built functions and connections to solve FinTech use cases. These include
- Bank Identification Number (BIN) Lookup: Identify cards and access card metadata to personalize user experience and securely process transactions with a simple API call. See BIN lookup.
- Network Tokenization: Replace sensitive account and card data with network-issued tokens that protect cardholder details while reducing fraud rates and costs. See Network Tokenization.
- Integrate with PSPs, Card Issuers, Financial Services Data providers, and more third-party applications. See catalog for the full list.
- Account Updater: A service that automatically updates vaulted customer card details (for example, new card numbers, expiration dates) to reduce failed transactions and improve authorization rates.
- 3DS: An authentication protocol that adds an extra layer of security for online card transactions by requiring cardholders to verify their identity, typically via a password, SMS code, or biometric verification.
Next steps
Create your first vault to get started.